sun.security.validator.ValidatorException: PKIX path building failed in Salesforce
Working on integration Salesforce with external system and vice versa through both REST and SOAP APIs you might get the following exception
sun.security.validator.ValidatorException:
PKIX path building failed:
sun.security.provider.certpath.SunCertPathBuilderException:
unable to find valid certification path to requested target
1. Salesforce to external system integration errors
The first thing to check is certificate on external system side. Most likely the problem is on this side.
1.1 The problem with certificate itself. Any issue with certificate on 3rd party side will cause the error. You can check this site for more details and examples on certificates issues.
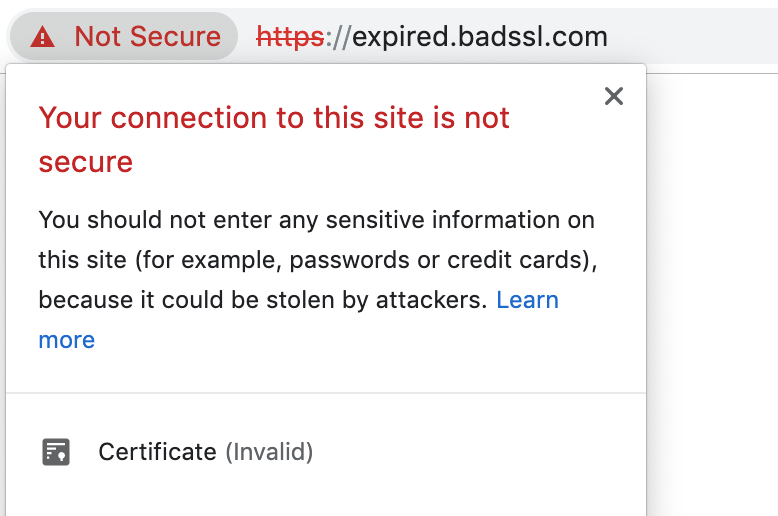
Here’re a few possible reason why certificate is not trusted:
- certificate is expired
- certificate is for a wrong host
- certificate is self-signed
- certificate with untrusted root
- certificate is revoked
- certificate is invalid by key pinning
The only possible solution for these cases is to install correct certificate on a server.
1.2 When certificate on a server is valid and you can access the host by browser with no error it might be a sign of a broken certificate chain of trust.
Salesforce’s certificate trust policy is to require server and client certificate chains to include all intermediate certificates that exist between the server or client certificate and the chain’s root certificate
You can review salesforce trusted certificates via https://YOUR-INSTANCE.salesforce.com/cacerts.jsp (https://slepenkov-dev-ed.my.salesforce.com/cacerts.jsp)
Most probably the server has no intermediate, root CA or several certificates installed/added and thus these certificates are not added to the server response during handshake.
On server you need to have all certificates in the chain. Different servers has different configuration and different locations for a certificates but in any case server must provide a whole chain to a client in order to be trusted. Structured in the following way

You can verify this case with the following command:
openssl s_client -connect techcrunch.com:443
Valid result will be as follow:

When chain is broken the same command will produce the following result:
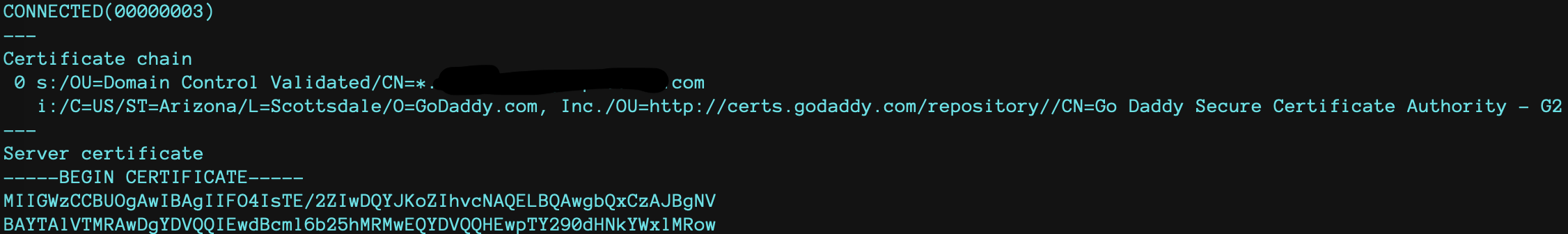
with final error messages
Verify return code: 21 (unable to verify the first certificate)
or
verify return code: 20 (unable to get local issuer certificate)
All you need to fix that is to add root CA certificate and/or intermediate certificates if needed in order to send server response with entire certificates chain during the handshake.
2. External System to Salesforce
When connecting to Salesforce from external application you might get the same error. This time error means that you server have no some salesforce chain of trust certificates. You can add it one by one or as a certificate bundle to your server.
Just download certificates chain with this command
openssl s_client -showcerts -connect slepenkov-dev-ed.my.salesforce.com:443
The output will contain all certificates in chain and you can copy and add it to your server certificate store.
